Monday, July 15, 2019
Data Representation
1) Number System:-
i) Concept of Non-Positional Number System:-- Roman Number System
ii) Concept of Positional Number System:-
- Decimal
- Binary
- Octal and
- Hexadecimal Number System
iii) Conversion
iv) Arithmetic
v) Different methods of Negative Number Representation
vi) Various Binary Coding Schemes
vii) Concept of Fixed and Floating Point Numbers
viii) Bit map representation of image
ix) Concept of Multimedia.
Saturday, July 13, 2019
B) NETWORKING
Syllabus:1) Introduction to Networking, 2) Components of a Network, 3) Network Topologies, 4) Network Connecting Devices, 5) LAN Protocols, 6) Switching Technique, 7) Use of MODEM, 8) TCP/IP Protocols, 9) IP Addressing, 10) Domain Name System, 11) URL, 12) Introduction to Internet, 13) HTML
********************************************
********************************************
1) Introduction to Networking
There are more than 2.5 billion devices currently connected to the internet, with almost 8 new internet users being added every second worldwide. If this does not amaze you, it is estimated that by 2020, more than 200 billion sensors will come online and report their data seamlessly over the internet. With such a rich ecosystem, the internet needs to be very rigid, well planned and structured. In this new series, I will try my best to cover the different network elements and protocols that build up this huge system.
What is Computer Networking?
By definition, a computer network is a group of computers that are linked together through a communication channel.
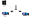

All the computer devices are called hosts or end systems. Hosts sending requests are called clients while hosts receiving requests are called servers. End systems are connected together by a network of communication links and packet switches. Communication links are made up of different types of physical media, including coaxial cable, copper wide, optical fiber, and radio spectrum. Different links can transmit data at different rates, with the transmission rate of a link measured in bits/second. When one end system has data to send to another end system, the sending end system segments the data and adds header bytes to each segment. The resulting packages of information, known as packets, are then sent through the network to the destination end system, where they are reassembled into the original data. A packet switch takes a packet arriving on one of its incoming communication links and forwards that packet on one of its outgoing communication links. Common packet switches are routers and link-layer switches.
*******************************************
2) Components of a Network:
i) Servers (File server, Communication Server, Print Server) and Workstation:
A server is a computer designed to process requests and deliver data to another computer over the internet or a local network. A server is a computer program or a device that provides functionality for other programs or devices.The purpose of a server is to share data as well as to share resources and distribute work. A server computer can serve its own computer programs. Each server has a unique name by which a user can identify the server.
Two types of servers are used in a network:-
i) Dedicated Server :
A server that is hosted by a company and only allows one company to lease and access it is called a dedicated server. It is "dedicated" to the one client and is not shared with any other clients. Dedicated servers usually allow the client to choose what operating system is installed on it and what type of hardware. A computer that is reserved for server's job and its only job is to help workstations to access data, software, and hardware resources are dedicated server. It does not allow a user to use it as workstation. It functions only as a storage area for data and software and allows access to hardware resources. Novell Netware server is an example of dedicated server.
ii) Non-Dedicated Server:--- A computer that allows to use itself as workstation and provides facilities of sharing its resources to other computers in the network is non-dedicated server. Windows NT, Advanced 2000 servers are examples of non-dedicated servers.
File Server:-A file server is a computer on a network that is used to provide users on a network with access to files.
Communication Server:- A communication server is a computer system designed to handle a wide array of communications-based applications. These servers connect to a wide variety of different platforms in a completely seamless manor, allowing different systems to talk to each other without interference. These servers are open and carrier-grade, which allows anyone to connect to them with the understanding that the communication will be both safe and reliable. The server’s communication focus and flexibility make it the backbone of many communication and Internet systems.
Print Server:-A Print Server is a computer or standalone device responsible for managing one or more printers on a network. Because of the load required for a print job, a print server does not need to be a fast computer.
Workstation:
A workstation is a computer dedicated to a user or group of users engaged in business or professional work. It includes one or more high resolution displays and a faster processor than a personal computer (PC). A workstation also has greater multitasking capability because of additional random access memory (RAM), drives and drive capacity. A workstation may also have a higher-speed graphics adapters and more connected peripherals.
.......................................................................................................................................................
ii) NIC:-
A network interface card (NIC) is a hardware component, typically a circuit board or chip, which is installed on a computer so that it can connect to a network. Modern NICs provide functionality to computers such as support for I/O interrupt, direct memory access (DMA) interfaces, data transmission, network traffic engineering and partitioning.
A NIC provides a computer with a dedicated, full-time connection to a network by implementing the physical layer circuitry necessary for communicating with a data link layer standard, such as Ethernet or Wi-Fi. Each card represents a device and can prepare, transmit and control the flow of data on the network. The NIC uses the OSI model to send signals at the physical layer, transmit data packets at the network layer and operate as an interface at the TCP/IP layer.
The network card operates as a middleman between a computer and a data network. For example, when a user requests a web page, the computer will pass the request to the network card which converts it into electrical impulses. Those impulses are received by a web server on the internet and responds by sending the web page back to the network card as electrical signals. The card gets these signals and translates them into the data that the computer displays.
Originally, network controllers were implemented as expansion cards that could be plugged into a computer port, router or USB device. However, more modern controllers are built directly into the computer motherboard chipset. Expansion card NICs can be purchased online or in retail stores if additional independent network connections are needed. When purchasing a NIC, specifications should correspond with the standard of the network.
The term network interface card is often considered interchangeable with the terms network interface controller, network adapter and LAN adapter.
Types of network interface cards
While the standard NIC is a plastic circuit board that slides into a computer to connect with the motherboard, there are multiple ways this connection can occur:
Wireless- These are NICs that use an antenna to provide wireless reception through radio frequency waves. Wireless NICs are designed for Wi-Fi connection.
Wired- These are NICs that have input jacks made for cables. The most popular wired LAN technology is Ethernet.
USB- These are NICs that provide network connections through a device plugged into the USB port.
Fiber optic- These are expensive and more complex NICs that are used as a high-speed support system for network traffic handling on server computers. This could also be accomplished by combining multiple NICs.
Components of network interface cards
Speed- All NICs have a speed rating in terms of Mbps that suggests the general performance of the card when implemented in a computer network with ample bandwidth. If the bandwidth is lower than the NIC or multiple computers are connected with the same controller, this will slow down the labeled speed. The average Ethernet NICs are offered in 10 Mbps, 100 Mbps, 1000 Mbps and 1 Gbps varieties.
Driver- This is the required software that passes data between the computer's operating system (OS) and the NIC. When a NIC is installed on a computer, the corresponding driver software is also downloaded. Drivers must stay updated and uncorrupted to ensure optimal performance from the NIC.
MAC address- Unique, unchangeable MAC addresses, also known as a physical network address, are assigned to NICs that is used to deliver Ethernet packets to the computer.
Connectivity LED- Most NICs have an LED indicator integrated into the connector to notify the user of when the network is connected and data is being transmitted.
Router- A router is also sometimes needed to allow communication between a computer and other devices. In this case, the NIC connects to the router which is connected to the internet.
........................................................................................................................................................
iii) Guided Media:
It is defined as the physical medium through which the signals are transmitted. It is also known as Bounded media.
Types Of Guided media:
A) Twisted pair:
Twisted pair is a physical media made up of a pair of cables twisted with each other. A twisted pair cable is cheap as compared to other transmission media. Installation of the twisted pair cable is easy, and it is a lightweight cable. The frequency range for twisted pair cable is from 0 to 3.5KHz.
A twisted pair consists of two insulated copper wires arranged in a regular spiral pattern.
The degree of reduction in noise interference is determined by the number of turns per foot. Increasing the number of turns per foot decreases noise interference.
Types of Twisted pair:
Unshielded Twisted Pair:
An unshielded twisted pair is widely used in telecommunication. Following are the categories of the unshielded twisted pair cable:
o Category 1: Category 1 is used for telephone lines that have low-speed data.
o Category 2: It can support upto 4Mbps.
o Category 3: It can support upto 16Mbps.
o Category 4: It can support upto 20Mbps. Therefore, it can be used for long-distance communication.
o Category 5: It can support upto 200Mbps.
Advantages Of Unshielded Twisted Pair:
o It is cheap.
o Installation of the unshielded twisted pair is easy.
o It can be used for high-speed LAN.
Disadvantage:
o This cable can only be used for shorter distances because of attenuation.
Shielded Twisted Pair
A shielded twisted pair is a cable that contains the mesh surrounding the wire that allows the higher transmission rate.
Characteristics Of Shielded Twisted Pair:
o The cost of the shielded twisted pair cable is not very high and not very low.
o An installation of STP is easy.
o It has higher capacity as compared to unshielded twisted pair cable.
o It has a higher attenuation.
o It is shielded that provides the higher data transmission rate.
Disadvantages
o It is more expensive as compared to UTP and coaxial cable.
o It has a higher attenuation rate.
B) Coaxial Cable:-
o Coaxial cable is very commonly used transmission media, for example, TV wire is usually a coaxial cable.
o The name of the cable is coaxial as it contains two conductors parallel to each other.
o It has a higher frequency as compared to Twisted pair cable.
o The inner conductor of the coaxial cable is made up of copper, and the outer conductor is made up of copper mesh. The middle core is made up of non-conductive cover that separates the inner conductor from the outer conductor.
o The middle core is responsible for the data transferring whereas the copper mesh prevents from the EMI(Electromagnetic interference).
Coaxial cable is of two types:
1. Baseband transmission: It is defined as the process of transmitting a single signal at high speed.
2. Broadband transmission: It is defined as the process of transmitting multiple signals simultaneously.
Advantages Of Coaxial cable:
o The data can be transmitted at high speed.
o It has better shielding as compared to twisted pair cable.
o It provides higher bandwidth.
Disadvantages Of Coaxial cable:
o It is more expensive as compared to twisted pair cable.
o If any fault occurs in the cable causes the failure in the entire network.
C) Fibre Optic
o Fibre optic cable is a cable that uses electrical signals for communication.
o Fibre optic is a cable that holds the optical fibres coated in plastic that are used to send the data by pulses of light.
o The plastic coating protects the optical fibres from heat, cold, electromagnetic interference from other types of wiring.
o Fibre optics provide faster data transmission than copper wires.
Diagrammatic representation of fibre optic cable:
Basic elements of Fibre optic cable:
o Core: The optical fibre consists of a narrow strand of glass or plastic known as a core. A core is a light transmission area of the fibre. The more the area of the core, the more light will be transmitted into the fibre.
o Cladding: The concentric layer of glass is known as cladding. The main functionality of the cladding is to provide the lower refractive index at the core interface as to cause the reflection within the core so that the light waves are transmitted through the fibre.
o Jacket: The protective coating consisting of plastic is known as a jacket. The main purpose of a jacket is to preserve the fibre strength, absorb shock and extra fibre protection.
Following are the advantages of fibre optic cable over copper:
o Greater Bandwidth: The fibre optic cable provides more bandwidth as compared copper. Therefore, the fibre optic carries more data as compared to copper cable.
o Faster speed: Fibre optic cable carries the data in the form of light. This allows the fibre optic cable to carry the signals at a higher speed.
o Longer distances: The fibre optic cable carries the data at a longer distance as compared to copper cable.
o Better reliability: The fibre optic cable is more reliable than the copper cable as it is immune to any temperature changes while it can cause obstruct in the connectivity of copper cable.
o Thinner and Sturdier: Fibre optic cable is thinner and lighter in weight so it can withstand more pull pressure than copper cable.
........................................................................................................................................................
iv) Unguided Media:
An unguided transmission transmits the electromagnetic waves without using any physical medium. Therefore it is also known as wireless transmission.
In unguided media, air is the media through which the electromagnetic energy can flow easily.
Unguided transmission is broadly classified into three categories:
Radio waves
Radio waves are the electromagnetic waves that are transmitted in all the directions of free space.
Radio waves are omnidirectional, i.e., the signals are propagated in all the directions.
The range in frequencies of radio waves is from 3Khz to 1 khz.
In the case of radio waves, the sending and receiving antenna are not aligned, i.e., the wave sent by the sending antenna can be received by any receiving antenna.
An example of the radio wave is FM radio.
Applications Of Radio waves:
A Radio wave is useful for multicasting when there is one sender and many receivers.
An FM radio, television, cordless phones are examples of a radio wave.
Advantages Of Radio transmission:
Radio transmission is mainly used for wide area networks and mobile cellular phones.
Radio waves cover a large area, and they can penetrate the walls.
Radio transmission provides a higher transmission rate.
Microwaves:-
Microwaves are of two types:
Terrestrial microwave
Satellite microwave communication.
Terrestrial Microwave Transmission
Terrestrial Microwave transmission is a technology that transmits the focused beam of a radio signal from one ground-based microwave transmission antenna to another.
Microwaves are the electromagnetic waves having the frequency in the range from 1GHz to 1000 GHz.
Microwaves are unidirectional as the sending and receiving antenna is to be aligned, i.e., the waves sent by the sending antenna are narrowly focussed.
In this case, antennas are mounted on the towers to send a beam to another antenna which is km away.
It works on the line of sight transmission, i.e., the antennas mounted on the towers are the direct sight of each other.
Characteristics of Microwave:
Frequency range: The frequency range of terrestrial microwave is from 4-6 GHz to 21-23 GHz.
Bandwidth: It supports the bandwidth from 1 to 10 Mbps.
Short distance: It is inexpensive for short distance.
Long distance: It is expensive as it requires a higher tower for a longer distance.
Attenuation: Attenuation means loss of signal. It is affected by environmental conditions and antenna size.
Advantages Of Microwave:
Microwave transmission is cheaper than using cables.
It is free from land acquisition as it does not require any land for the installation of cables.
Microwave transmission provides an easy communication in terrains as the installation of cable in terrain is quite a difficult task.
Communication over oceans can be achieved by using microwave transmission.
Disadvantages of Microwave transmission:
Eavesdropping: An eavesdropping creates insecure communication. Any malicious user can catch the signal in the air by using its own antenna.
Out of phase signal: A signal can be moved out of phase by using microwave transmission.
Susceptible to weather condition: A microwave transmission is susceptible to weather condition. This means that any environmental change such as rain, wind can distort the signal.
Bandwidth limited: Allocation of bandwidth is limited in the case of microwave transmission.
Satellite Microwave Communication
A satellite is a physical object that revolves around the earth at a known height.
Satellite communication is more reliable nowadays as it offers more flexibility than cable and fibre optic systems.
We can communicate with any point on the globe by using satellite communication.
How Does Satellite work?
The satellite accepts the signal that is transmitted from the earth station, and it amplifies the signal. The amplified signal is retransmitted to another earth station.
Advantages Of Satellite Microwave Communication:
The coverage area of a satellite microwave is more than the terrestrial microwave.
The transmission cost of the satellite is independent of the distance from the centre of the coverage area.
Satellite communication is used in mobile and wireless communication applications.
It is easy to install.
It is used in a wide variety of applications such as weather forecasting, radio/TV signal broadcasting, mobile communication, etc.
Disadvantages Of Satellite Microwave Communication:
Satellite designing and development requires more time and higher cost.
The Satellite needs to be monitored and controlled on regular periods so that it remains in orbit.
The life of the satellite is about 12-15 years. Due to this reason, another launch of the satellite has to be planned before it becomes non-functional.
Infrared
An infrared transmission is a wireless technology used for communication over short ranges.
The frequency of the infrared in the range from 300 GHz to 400 THz.
It is used for short-range communication such as data transfer between two cell phones, TV remote operation, data transfer between a computer and cell phone resides in the same closed area.
Characteristics Of Infrared:
It supports high bandwidth, and hence the data rate will be very high.
Infrared waves cannot penetrate the walls. Therefore, the infrared communication in one room cannot be interrupted by the nearby rooms.
An infrared communication provides better security with minimum interference.
Infrared communication is unreliable outside the building because the sun rays will interfere with the infrared waves.
..........................................................................................................................................................
vi) Network Operating System - Characteristics:-
A network operating system is a specialized operating system for a network device such as a router, switch or firewall. A network operating system is a software application that provides a platform for both the functionality of an individual computer and for multiple computers within an interconnected network. Basically, a network operating system controls other software and computer hardware to run applications, share resources, protect data and establish communication. Individual computers run client operating systems, while network systems create the software infrastructure for wireless, local and wide area networks to function.
A network operating system (NOS) provides services to clients over a network. Both the client/server and peer-to-peer networking models use network operating systems, and as such, NOSes must be able to handle typical network duties such as the following:
· Providing access to remote printers, managing which users are using which printers when, managing how print jobs are queued, and recognizing when devices aren't available to the network
· Enabling and managing access to files on remote systems, and determining who can access what—and who can't
· Granting access to remote applications and resources, such as the Internet, and making those resources seem like local resources to the user (the network is ideally transparent to the user)
· Providing routing services, including support for major networking protocols, so that the operating system knows what data to send where
· Monitoring the system and security, so as to provide proper security against viruses, hackers, and data corruption.
· Providing basic network administration utilities (such as SNMP, or Simple Network Management Protocol), enabling an administrator to perform tasks involving managing network resources and users.
A) UNIX / Linux:
UNIX, created originally by Bell Labs (under AT and T), is a powerful server operating system that can be used in peer-to-peer or client/server networks. UNIX was the first operating system written in the C programming language. Due to an antitrust ruling forbidding AT and T from releasing operating systems commercially, AT and T released UNIX upon its completion in 1974 to universities, mostly, enabling people to go in and actually view the source code to the system, which enabled coders to reconstruct the basic functions of the original UNIX operating system. From this practice, called reverse engineering, came Linux, which was first developed in the late 1980s by a young student at the University of Helsinki in Finland named Linus Torvalds.
UNIX (and Linux by extension) systems offer the following features:
· Fully protected multitasking: This means that UNIX can easily switch between tasks without the operating system crashing, because all UNIX processes are separate from those of the operating system. Even if an application crashes, unless it somehow manages to take down the X Windows system with it (which does happen), the operating system just keeps right on humming.
· High performance and stability : Many servers running UNIX or Linux have run for years without crashing once. The multitasking capabilities of UNIX, along with the rapid rate at which the operating system matures (especially with Linux, which is free and can be changed by anyone), make UNIX or Linux a powerful solution, especially for server systems.
· Multi-user capabilities : True multiuser systems enable different users to be logged in to the same system simultaneously. In UNIX and Linux, not only can a user log in to the same system at the same time as other users, that user can log in multiple times on the same system as the same user without the operating system batting an eyelash (such things are often necessary when administrating a network, particularly when managing users).
· Tons of high-quality software : From Apache Server (a Web server that’s used on a whopping 6 in 10 major Web servers on the Internet) to the long-awaited Mozilla.org Mozilla 1.0 open source Web browser/e-mail software (Mozilla is an open source version of the venerated Netscape Communicator) to the powerful free Gimp graphics manipulation software, Linux is packed with tons of free, high-quality software. The trick is that, with UNIX/Linux, you give up compatibility with commercial software that’s available only for Windows and/or Macintosh, currently.
· Easy customization : While other operating systems seem to offer less and less choice to the user about which applications to install with the operating system (Windows XP is this way), UNIX and especially Linux are the exact counterpoint to that model. With UNIX or Linux, you can actually customize your operating system kernel, stripping it down to just drivers and networking or installing everything possible.
· Modular architecture : The modular architecture of UNIX (and especially Linux) is directly responsible for how customizable UNIX is. Modular really means just what it sounds like: The operating system is built with a kernel that attaches modules to itself based on what the user needs.
· POSIX compliance: With a free operating system like UNIX, the different distributions (or flavors) of UNIX quickly became difficult to manage. Currently, hundreds of different implementations of UNIX are available. To enable programmers to have some idea of how to code their software such that it would run on any version of UNIX, the Institute of Electrical and Electronics Engineers, Inc. (IEEE) defined the Portable Operating System Interface (POSIX).
· Use of TCP/IP as the standard protocol stack: UNIX overwhelmingly uses TCP/IP as the protocol stack of choice. If you consider that the vast majority of the servers that help make up the Internet are UNIX computers of one form or another, you start to get the idea why TCP/IP is so popular.
· A shell interface: All versions of UNIX (at least those you care about for the exam) include a shell interface of some sort. If you have ever seen your computer use a completely black screen with white words written on it, that’s a shell interface. You simply type in commands at the prompt and hit Enter to execute those commands. The hard part in using these interfaces is simply the effort it takes to learn all of those rather cryptic commands. Making life even more difficult, UNIX is ultimately customizable and can use different shells. The bash shell (likely the most popular shell in use today) and the tcsh shell, for example, have different commands for the same action.
· A graphical user interface: Although most versions of UNIX (such as Red Hat Linux) include a graphical user interface (GUI) these days, this has not always been the case. Historically, UNIX has been derided for its cryptic interface, and the advent of the GUI into popular UNIX systems was a direct result of this. Popular UNIX GUIs include KDE and GNOME. KDE is mostly used with Linux, but GNOME has versions for the Sun Solaris operating system, and therefore crosses the border from Linux into UNIX proper.
· Support for dumb terminals: Traditionally, UNIX was used for dumb terminals, and just about all versions of UNIX still include this capability. The traditional dumb terminal model involves one central UNIX server that is used by remote terminals to execute applications. Basically, a user logs in to a UNIX system via Telnet or some other remote connectivity application and uses UNIX commands to tell the remote system what functions to perform. In this way, users can download and check e-mail via a text-based e-mail client such as Pine. The dumb terminal in this form isn’t used much anymore; Web browsers are definitely more than just dumb terminals— and Web browsers are now the clients most often seen by UNIX servers (at least those that make up the Internet). However, wireless devices such as cell phones and mobile Internet e-mail clients such as AOL’s Mobile Communicator device are good examples of modern dumb terminals. The devices have nearly no storage at all, and don’t carry large e-mail clients on the device; the message is simply transferred as text from one end to the other.
Interoperability
Open source software such as SAMBA is used to provide Windows users with Server Message Block (SMB) file sharing.
Authentication:-Centralized login authentication
File and Print Services
Network File System (NFS) is a distributed file system that allows users to access files and directories located on remote computers and treat those files and directories as if they were local.
LPR/LPD is the primary UNIX printing protocol used to submit jobs to the printer. The LPR component initiates commands such as "print waiting jobs," "receive job," and "send queue state," and the LPD component in the print server responds to them.
Security
With most Unix operating systems, the network services can be individually controlled to increase security.
B) Netware
NetWare has been a great LAN operating system for years, but only recently (with NetWare 5.x has NetWare moved beyond the LAN to where it can easily be a part of larger networks. Until quite recently, Novell NetWare used to be the single most-used network operating system (NOS). However, first Windows NT, and Windows 2000 and Linux, have steadily eaten into the NetWare market share for network operating systems. Currently, all three operating systems have a roughly equal share of the network operating system market, which means that NetWare is still used in at least one-third of all server systems.
NetWare features
NetWare offers the following features :
· Multiprocessor kernel: This feature enables one NetWare operating system to utilize multiple processors. This process is called symmetric multiprocessing (SMP). SMP enables processors to share memory and bus paths, even coordinating the processing of a single application in parallel.
· NLMs: Where UNIX uses daemons and Windows uses services, NetWare uses NetWare Loadable Modules (or NLMs) to provide services from the server. NLMs are programs that run in the background on the server to provide consistent services to the network.
· PCI Hot Plug: This feature enables administrators to dynamically configure PCI network components while the system is running. You can replace, upgrade, or add new cards with the Hot replace, Hot upgrade, and Hot expansion features, respectively.
Client Support
NetWare 5 comes with Novell Client software for three client platforms: DOS and Windows 3.1x, Windows 95/98, and Windows NT.
Interoperability
You can set the Novell Clients for Windows 95/98 and Windows NT to work with one of three network protocol options: IP only, IP and IPX, or IPX only.
Authentication
Centralized login authentication
File and Print Services
File Services NetWare offers two choices of mutually compatible file services: Novell Storage Services (NSS) and the traditional NetWare File System. Both kinds of file services let you store, organize, manage, access, and retrieve data on the network. NSS gathers all unpartitioned free space that exists on all the hard drives connected to your server, together with any unused space in NetWare volumes, and places it into a storage pool. You create NSS volumes from this storage pool during server installation or later through NWCONFIG. Novell Distributed Print Services (NDPS) is the default and preferred print system in NetWare. NDPS supports IP-based as well as IPX-based printing.
Security
Novell has support for a public key infrastructure built into NetWare 5 using a public certificate, developed by RSA Security.
C) Windows
Directory Services
A directory service is a database of user accounts and other information that network administrators use to control access to shared network resources. When users connect to a network, they have to be authenticated before they can access network resources. Authentication is the process of checking the user's credentials (usually a user name and a password) against the directory. Users that supply the proper credentials are permitted access according to the permissions specified by the network administrator.
Client Support
Windows 3.x, Windows 95, Windows 98, and Windows NT Workstation 4.0 Windows 2000 Professional, Xp Pro. Vista Ultimate, Vista Business.
Interoperability
Windows 2000,2003,2008 Server supports UNIX, Novell NetWare, Windows NT Server 4.0, and Macintosh.
Authentication
Successful user authentication in a Windows 2000,2003,2008 computing environment consists of separate processes: interactive logon, which confirms the user's identification to either a domain account or a local computer, and network authentication, which confirms the user's identification to any network service that the user attempts to access.
Types of authentication
Kerberos V5 is used with either a password or a smart card for interactive logon. It is also the default method of network authentication for services.The Kerberos V5 protocol verifies both the identity of the user and network services Secure Socket Layer/Transport Layer Security (SSL/TLS) authentication, is used when a user attempts to access a secure Web server.
File and Print Services
You can add and maintain printers in Windows server using the print administration wizard, and you can add file shares using Active Directory management tools. Windows server also offers Distributed File Services, which let you combine files on more than one server into a single share.
Active Directory
After many years of anticipation, Microsoft introduced an enterprise directory service in the Windows 2000 Server product line, called Active Directory. It uses a hierarchical tree design comprised of container and leaf objects. The fundamental unit of organization in Active Directory directory service is the domain, but; you can group domains together into a tree, and even group multiple trees together into a forest. Domains that are in the same tree automatically have bidirectional trust relationships established between them, which eliminates the need for administrators to create them manually. The trust relationships are also transitive , meaning that if Domain A trusts Domain B and Domain B trusts Domain C, then Domain A trusts Domain C.
Security
User-level security protects shared network resources by requiring that a security provider authenticate a user’s request to access resources. The domain controller , grants access to the shared resource by verifying that the user name and password are the same as those on the user account list stored on the network security provider. Because the security provider maintains a network-wide list
of user accounts and passwords, each client computer does not have to store a list of accounts. Share-level security protects shared network resources on the computer with individually assigned passwords. For example, you can assign a password to a folder or a locally attached printer. If other users want to access it, they need to type in the appropriate password. If you do not assign a password to a shared resource, every user with access to the network can access that resource.
......................................................................................................................................................
************************************************************
3) Network Topologies:
Definition:
A Network Topology is the arrangement with which computer systems or network devices are connected to each other. ... Both logical and physical topologies could be same or different in a same network.
Types of Network Topologies:-
There are four categories: Star topology, Bus topology, Ring topology and Mesh topology. Hybrid combinations of these topologies also exist. Star topology – all computers and devices are connected to a main hub or switch.
A network topology is the arrangement of nodes -- usually switches, routers, or software switch/router features -- and connections in a network, often represented as a graph. The topology of the network, and the relative locations of the source and destination of traffic flows on the network, determine the optimum path for each flow and the extent to which redundant options for routing exist in the event of a failure. There are two ways of defining network geometry: the physical topology and the logical (or signal) topology.
The physical topology of a network is the layout of nodes and physical connections, including wires (Ethernet, DSL), fiber optics, and microwave. There are several common physical topologies, as described below and as shown in the illustration.
Types of physical topologies
In the bus network topology, every node is connected in series along a linear path. This arrangement is found today primarily in cable broadband distribution networks.
In the star network topology, a central node has a direct connection to all other nodes. Switched local-area networks (LANs) based on Ethernet switches, including most wired home and office networks, have a physical star topology.
In the ring network topology, the nodes are connected in a closed loop configuration. Some rings will pass data only in one direction, while others are capable of transmission in both directions. These bidirectional ring networks are more resilient than bus networks because traffic can reach a node by moving in either direction. Metro networks based on Synchronous Optical Network Technology (SONET) are the primary example of ring networks today.
The mesh network topology links nodes with connections so that multiple paths between at least some points of the network are available. A network is said to be fully meshed if all nodes are directly connected to all other nodes, and partially meshed if only some nodes have multiple connections to others. Meshing to create multiple paths increases resiliency under failure, but increases cost. The Internet is a mesh network.
The tree network topology, also called a star of stars, is a network where star topologies are themselves connected in a star configuration. Many larger Ethernet switch networks including data center networks, are configured as trees.
Logical topologies
A logical topology for a network usually refers to the relationship between nodes and logical connections. A logical connection will differ from a physical path when information can take an invisible hop at intermediate points. In optical networks, optical add-drop multiplexers (ADMs) create logical optical paths because the ADM hop isn't visible to the endpoint nodes. Networks based on virtual circuits (or tunnels) will have a physical topology based on the real connection medium (fiber, for example) and a logical topology based on the circuits/tunnels.
Sometimes the logical topology will refer to the topology as the user sees it, which means the connectivity of the network. IP and Ethernet networks, the two most commonly used today, are fully meshed at the connection level because any user can connect with any other -- unless some means of blocking unwanted connections, like a firewall, is introduced. This full connectivity is a property of the network protocols used (IP and Ethernet), not of the network topology itself. Any network topology can appear to be fully meshed to its users
****************************************************************
4) Network Connecting Devices:-
1. Repeater – A repeater operates at the physical layer. Its job is to regenerate the signal over the same network before the signal becomes too weak or corrupted so as to extend the length to which the signal can be transmitted over the same network. An important point to be noted about repeaters is that they do not amplify the signal. When the signal becomes weak, they copy the signal bit by bit and regenerate it at the original strength. It is a 2 port device.
2. Hub – A hub is basically a multiport repeater. A hub connects multiple wires coming from different branches, for example, the connector in star topology which connects different stations. Hubs cannot filter data, so data packets are sent to all connected devices. In other words, collision domain of all hosts connected through Hub remains one. Also, they do not have intelligence to find out best path for data packets which leads to inefficiencies and wastage.
Types of Hub
- Active Hub :- These are the hubs which have their own power supply and can clean , boost and relay the signal along the network. It serves both as a repeater as well as wiring center. These are used to extend maximum distance between nodes.
- Passive Hub :- These are the hubs which collect wiring from nodes and power supply from active hub. These hubs relay signals onto the network without cleaning and boosting them and can’t be used to extend distance between nodes.
3. Bridge – A bridge operates at data link layer. A bridge is a repeater, with add on functionality of filtering content by reading the MAC addresses of source and destination. It is also used for interconnecting two LANs working on the same protocol. It has a single input and single output port, thus making it a 2 port device.
Types of Bridges
- Transparent Bridges :- These are the bridge in which the stations are completely unaware of the
bridge’s existence i.e. whether or not a bridge is added or deleted from the network , reconfiguration of
the stations is unnecessary. These bridges makes use of two processes i.e. bridge forwarding and bridge learning. - Source Routing Bridges :- In these bridges, routing operation is performed by source station and the frame specifies which route to follow. The hot can discover frame by sending a specical frame called discovery frame, which spreads through the entire network using all possible paths to destination.
4. Switch – A switch is a multi port bridge with a buffer and a design that can boost its efficiency(large number of ports imply less traffic) and performance. Switch is data link layer device. Switch can perform error checking before forwarding data, that makes it very efficient as it does not forward packets that have errors and forward good packets selectively to correct port only. In other words, switch divides collision domain of hosts, but broadcast domain remains same.
5. Routers – A router is a device like a switch that routes data packets based on their IP addresses. Router is mainly a Network Layer device. Routers normally connect LANs and WANs together and have a dynamically updating routing table based on which they make decisions on routing the data packets. Router divide broadcast domains of hosts connected through it.
6. Gateway – A gateway, as the name suggests, is a passage to connect two networks together that may work upon different networking models. They basically works as the messenger agents that take data from one system, interpret it, and transfer it to another system. Gateways are also called protocol converters and can operate at any network layer. Gateways are generally more complex than switch or router.
7. Brouter – It is also known as bridging router is a device which combines features of both bridge and router. It can work either at data link layer or at network layer. Working as router, it is capable of routing packets across networks and working as bridge, it is capable of filtering local area network traffic.
*******************************************************************
5) LAN Protocols:-
"Local Area Networks," or LANs, and "Wide Area Networks," or WANs, can both be defined by the network protocols that constitute them. Protocols are standards that define how data is ultimately transferred from one system to another. ... Two systems must be using the same LAN or WAN protocol to communicate.
LAN (Local Area Network) can use several Network Protocols to define the Network. These protocols are defined at the OSI Data Link Layer
| Protocol | Cable used | Topology | Media Access | Advantages | Disadvantages |
| Ethernet | Twisted Pair or Fiber Optic | Star | CSMA/CD | Fast; Easy setup and maintenance | Possible Collision issues |
| Token Ring | Twisted Pair | Ring | Token Passing | Low error rate | Slow (4 or 16 Mbps) |
| FDDI | Fiber Optic (Dual counter rotating ring) | Ring | Token Passing | Low error rate. Redundancy. | Expensive |
| ARCNet | Coaxial | Star | Token Passing | Predicable Network Performance | Slow. (Almost extinct) |
Ethernet :-
Ethernet is most widely used LAN Technology, which is defined under IEEE standards 802.3. The reason behind its wide usability is Ethernet is easy to understand, implement, maintain and allows low-cost network implementation. Also, Ethernet offers flexibility in terms of topologies which are allowed. Ethernet operates in two layers of the OSI model, Physical Layer, and Data Link Layer. For Ethernet, the protocol data unit is Frame since we mainly deal with DLL. In order to handle collision, the Access control mechanism used in Ethernet is CSMA/CD.
Ethernet LANs consist of network nodes and interconnecting media or link. The network nodes can be of two types:
Data Terminal Equipment (DTE):- Generally, DTEs are the end devices that convert the user information into signals or reconvert the received signals. DTEs devices are: personal computers, workstations, file servers or print servers also referred to as end stations. These devices are either the source or the destination of data frames. The data terminal equipment may be a single piece of equipment or multiple pieces of equipment that are interconnected and perform all the required functions to allow the user to communicate. A user can interact to DTE or DTE may be a user.
Data Terminal Equipment (DTE):- Generally, DTEs are the end devices that convert the user information into signals or reconvert the received signals. DTEs devices are: personal computers, workstations, file servers or print servers also referred to as end stations. These devices are either the source or the destination of data frames. The data terminal equipment may be a single piece of equipment or multiple pieces of equipment that are interconnected and perform all the required functions to allow the user to communicate. A user can interact to DTE or DTE may be a user.
Data Communication Equipment (DCE):- DCEs are the intermediate network devices that receive and forward frames across the network. They may be either standalone devices such as repeaters, network switches, routers or maybe communications interface units such as interface cards and modems. The DCE performs functions such as signal conversion, coding and may be a part of the DTE or intermediate equipment.
Currently, these data rates are defined for operation over optical fibers and twisted-pair cables:
i) Fast Ethernet
Fast Ethernet refers to an Ethernet network that can transfer data at a rate of 100 Mbit/s.
i) Fast Ethernet
Fast Ethernet refers to an Ethernet network that can transfer data at a rate of 100 Mbit/s.
ii) Gigabit Ethernet
Gigabit Ethernet delivers a data rate of 1,000 Mbit/s (1 Gbit/s).
Gigabit Ethernet delivers a data rate of 1,000 Mbit/s (1 Gbit/s).
iii) 10 Gigabit Ethernet
10 Gigabit Ethernet is the recent generation and delivers a data rate of 10 Gbit/s (10,000 Mbit/s). It is generally used for backbones in high-end applications requiring high data rates.
10 Gigabit Ethernet is the recent generation and delivers a data rate of 10 Gbit/s (10,000 Mbit/s). It is generally used for backbones in high-end applications requiring high data rates.
TOKEN RING:
A token ring network is a local area network (LAN) in which all computers are connected in a ring or star topology and pass one or more logical tokens from host to host. Only a host that holds a token can send data, and tokens are released when receipt of the data is confirmed. Token ring networks prevent data packets from colliding on a network segment because data can only be sent by a token holder and the number of tokens available is controlled.The most broadly deployed token ring protocols were IBM's, released in the mid-1980s, and the standardized version of it known as IEEE 82.5, which appeared in the late 1980s. The IEEE standard version provides for data transfer rates of 4, 16 or 100 Mbps.
Token ring was once widely used on LANs, but has been nearly entirely displaced by Ethernet thanks to pricing -- token ring products tended to be more expensive than Ethernet at similar speeds -- and thanks to the development of Ethernet switching and full-duplex links, which eliminated collisions as a practical concern in most situations.
Very briefly, here is how token ring works:
1. Systems in the LAN are arranged in a logical ring; each system receives data frames from its logical predecessor on the ring and sends them to its logical successor. The network may be an actual ring, with cabling connecting each node directly to its neighbors, but more often is a star, with the ring existing only logically in the wiring closet within the "multi access unit" to which all the hosts connect.
2. Empty information frames are continuously circulated on the ring, along with frames containing actual data; any node receiving an empty frame and having nothing to send simply forwards the empty frame.
3. When a computer has a message to send, it waits for an empty frame. When it has one, it does the following:
a) Inserts a token indicating that it is sending data in the frame -- this may be as simple as changing a zero to a one in the token section of the frame, although other schemes are possible, and is said to "hold the token" for that frame.
b) Inserts the data it wants to transmit into the payload section of the frame.
c) Sets a destination identifier on the frame.
4. When a computer receives a frame containing data (indicated by the token) it knows it cannot transmit data of its own and so it does the following:
a) If it is not the sender or the destination, it simply retransmits the frame, sending it to the next host in the ring.
b) If it is the destination for the message, it copies the message from the frame and clears the token to indicate receipt.
c) If it is the sender (and assuming the destination node has indicated receipt of the frame by clearing the token) it sees that the message has been received, removes the message payload from the frame (restoring it to "empty" status) and sends the empty frame around the ring.
The Fiber Distributed Data Interface(FDDI) also uses a token ring protocol.
********************************************************************
6) Switching Technique:
Introduction
Aim of Data Communication and Networking is to facilitate the exchange of data such as audio, text or video between various points in the world. This transfer of data takes place over the computer network over which the data travels smoothly. For the delivery of data or information with the ease of accuracy various types of Switching Techniques are employed in the Data Communication and Networking. Here in this post brief description of various types of Switching Techniques including Packet Switching, Message Switching and Circuit Switching techniques is given.
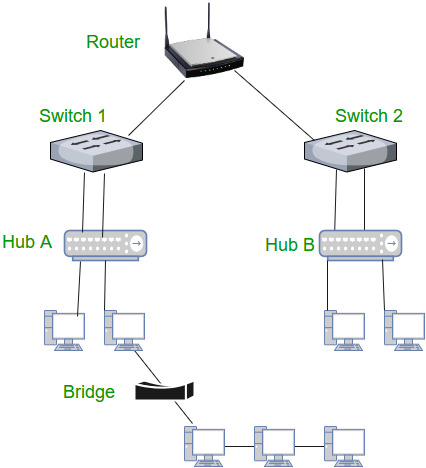
Types of Switching Techniques
There are basically three types of switching methods are made available. Out of three methods, circuit switching and packet switching are commonly used but the message switching has been opposed out in the general communication procedure but is still used in the networking application.
1) Circuit Switching
2) Packet Switching
3) Message Switching
2) Packet Switching
3) Message Switching
Circuit Switching
Circuit Switching is generally used in the public networks. It come into existence for handling voice traffic in addition to digital data. How ever digital data handling by the use of circuit switching methods are proved to be inefficient. The network for Circuit Switching is shown in figure.
- Here the network connection allows the electrical current and the associated voice with it to flow in between the two respective users. The end to end communication was established during the duration of call.
- In circuit switching the routing decision is made when the path is set up across the given network. After the link has been sets in between the sender and the receiver then the information is forwarded continuously over the provided link.
- In Circuit Switching a dedicated link/path is established across the sender and the receiver which is maintained for the entire duration of conversation.
Packet Switching
In Packet Switching, messages are broken up into packets and each of which includes a header with source, destination and intermediate node address information. Individual Packets in packet switching technique take different routes to reach their respective destination. Independent routing of packets is done in this case for following reasons:
- Bandwidth is reduces by the splitting of data onto different routes for a busy circuit.
- For a certain link in the network, the link goes down during transmission the the remaining packet can be sent through the another route.
- The major advantage of Packet switching is that they they are used for performing data rate conversion.
- When traversing the network switches, routers or the other network nodes then the packets are buffered in the queue, resulting in variable delay and throughput depending on the network’s capacity and the traffic load on network.
- Packet switching contrasts with another principal networking paradigm, circuit switching, a method which sets up a limited number of dedicated connections of constant bit rate and constant delay between nodes for exclusive use during the communication session.
- In cases where traffic fees are charged, for example in cellular communication, packet switching is characterized by a fee per unit of information transmitted.
Message Switching
In case of Message Switching it is not necessary to established a dedicated path in between any two communication devices. Here each message is treated as an independent unit and includes its own destination source address by its own. Each complete message is then transmitted from one device to another through internetwork.
- Each intermediate device receive the message and store it until the nest device is ready to receive it and then this message is forwarded to the next device. For this reason a message switching network is sometimes called as Store and Forward Switching.
- Message switches can be programmed with the information about the most efficient route as well as information regarding to the near switches that can be used for forwarding the present message to their required destination.
- The storing and Forwarding introduces the concept of delay. For this reasons this switching is not recommended for real time applications like voice and video.
---Switching techniques
In large networks, there can be multiple paths from sender to receiver. The switching technique will decide the best route for data transmission.
Switching technique is used to connect the systems for making one-to-one communication.
Classification Of Switching Techniques
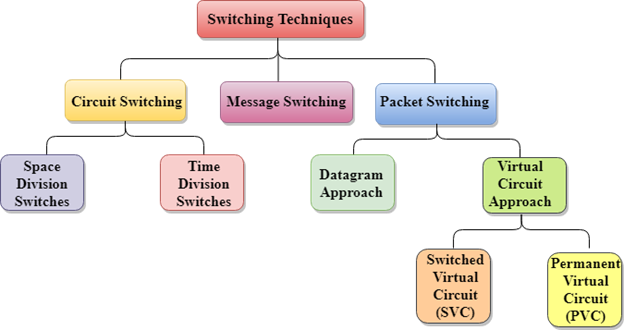
Circuit Switching
- Circuit switching is a switching technique that establishes a dedicated path between sender and receiver.
- In the Circuit Switching Technique, once the connection is established then the dedicated path will remain to exist until the connection is terminated.
- Circuit switching in a network operates in a similar way as the telephone works.
- A complete end-to-end path must exist before the communication takes place.
- In case of circuit switching technique, when any user wants to send the data, voice, video, a request signal is sent to the receiver then the receiver sends back the acknowledgment to ensure the availability of the dedicated path. After receiving the acknowledgment, dedicated path transfers the data.
- Circuit switching is used in public telephone network. It is used for voice transmission.
- Fixed data can be transferred at a time in circuit switching technology.
- Circuit establishment
- Data transfer
- Circuit Disconnect
 Circuit Switching can use either of the two technologies:
Circuit Switching can use either of the two technologies:
Space Division Switches:
- Space Division Switching is a circuit switching technology in which a single transmission path is accomplished in a switch by using a physically separate set of crosspoints.
- Space Division Switching can be achieved by using crossbar switch. A crossbar switch is a metallic crosspoint or semiconductor gate that can be enabled or disabled by a control unit.
- The Crossbar switch is made by using the semiconductor. For example, Xilinx crossbar switch using FPGAs.
- Space Division Switching has high speed, high capacity, and nonblocking switches.
- Crossbar Switch
- Multistage Switch
Crossbar Switch
The Crossbar switch is a switch that has n input lines and n output lines. The crossbar switch has n2 intersection points known as crosspoints.
Disadvantage of Crossbar switch:
The number of crosspoints increases as the number of stations is increased. Therefore, it becomes very expensive for a large switch. The solution to this is to use a multistage switch.
Multistage Switch
- Multistage Switch is made by splitting the crossbar switch into the smaller units and then interconnecting them.
- It reduces the number of crosspoints.
- If one path fails, then there will be an availability of another path.
- In the case of Circuit Switching technique, the communication channel is dedicated.
- It has fixed bandwidth.
- Once the dedicated path is established, the only delay occurs in the speed of data transmission.
- It takes a long time to establish a connection approx 10 seconds during which no data can be transmitted.
- It is more expensive than other switching techniques as a dedicated path is required for each connection.
- It is inefficient to use because once the path is established and no data is transferred, then the capacity of the path is wasted.
- In this case, the connection is dedicated therefore no other data can be transferred even if the channel is free.
Message Switching
- Message Switching is a switching technique in which a message is transferred as a complete unit and routed through intermediate nodes at which it is stored and forwarded.
- In Message Switching technique, there is no establishment of a dedicated path between the sender and receiver.
- The destination address is appended to the message. Message Switching provides a dynamic routing as the message is routed through the intermediate nodes based on the information available in the message.
- Message switches are programmed in such a way so that they can provide the most efficient routes.
- Each and every node stores the entire message and then forward it to the next node. This type of network is known as store and forward network.
- Message switching treats each message as an independent entity.
 Advantages Of Message Switching
Advantages Of Message Switching
- Data channels are shared among the communicating devices that improve the efficiency of using available bandwidth.
- Traffic congestion can be reduced because the message is temporarily stored in the nodes.
- Message priority can be used to manage the network.
- The size of the message which is sent over the network can be varied. Therefore, it supports the data of unlimited size.
- The message switches must be equipped with sufficient storage to enable them to store the messages until the message is forwarded.
- The Long delay can occur due to the storing and forwarding facility provided by the message switching technique.
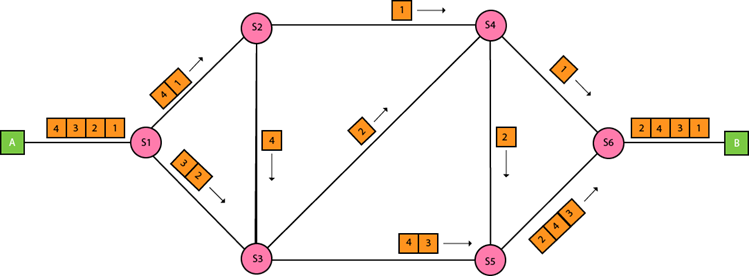
Packet Switching
- The packet switching is a switching technique in which the message is sent in one go, but it is divided into smaller pieces, and they are sent individually.
- The message splits into smaller pieces known as packets and packets are given a unique number to identify their order at the receiving end.
- Every packet contains some information in its headers such as source address, destination address and sequence number.
- Packets will travel across the network, taking the shortest path as possible.
- All the packets are reassembled at the receiving end in correct order.
- If any packet is missing or corrupted, then the message will be sent to resend the message.
- If the correct order of the packets is reached, then the acknowledgment message will be sent.
Approaches Of Packet Switching:
There are two approaches to Packet Switching:
Datagram Packet switching:
- It is a packet switching technology in which packet is known as a datagram, is considered as an independent entity. Each packet contains the information about the destination and switch uses this information to forward the packet to the correct destination.
- The packets are reassembled at the receiving end in correct order.
- In Datagram Packet Switching technique, the path is not fixed.
- Intermediate nodes take the routing decisions to forward the packets.
- Datagram Packet Switching is also known as connectionless switching.
Virtual Circuit Switching
- Virtual Circuit Switching is also known as connection-oriented switching.
- In the case of Virtual circuit switching, a preplanned route is established before the messages are sent.
- Call request and call accept packets are used to establish the connection between sender and receiver.
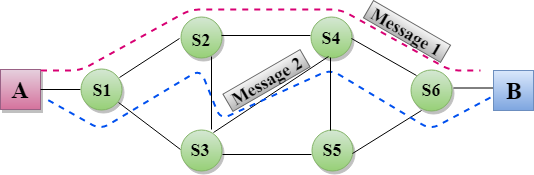
- In this case, the path is fixed for the duration of a logical connection.
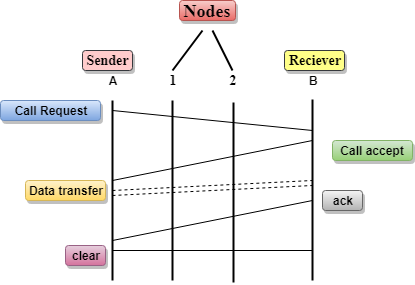
- In the above diagram, A and B are the sender and receiver respectively. 1 and 2 are the nodes.
- Call request and call accept packets are used to establish a connection between the sender and receiver.
- When a route is established, data will be transferred.
- After transmission of data, an acknowledgment signal is sent by the receiver that the message has been received.
- If the user wants to terminate the connection, a clear signal is sent for the termination.
Differences b/w Datagram approach and Virtual Circuit approach
Advantages Of Packet Switching:Datagram approach Virtual Circuit approach Node takes routing decisions to forward the packets. Node does not take any routing decision. Congestion cannot occur as all the packets travel in different directions. Congestion can occur when the node is busy, and it does not allow other packets to pass through. It is more flexible as all the packets are treated as an independent entity. It is not very flexible.
- Cost-effective: In packet switching technique, switching devices do not require massive secondary storage to store the packets, so cost is minimized to some extent. Therefore, we can say that the packet switching technique is a cost-effective technique.
- Reliable: If any node is busy, then the packets can be rerouted. This ensures that the Packet Switching technique provides reliable communication.
- Efficient: Packet Switching is an efficient technique. It does not require any established path prior to the transmission, and many users can use the same communication channel simultaneously, hence makes use of available bandwidth very efficiently.
- Packet Switching technique cannot be implemented in those applications that require low delay and high-quality services.
- The protocols used in a packet switching technique are very complex and requires high implementation cost.
- If the network is overloaded or corrupted, then it requires retransmission of lost packets. It can also lead to the loss of critical information if errors are nor recovered.
*********************************************************************
7) Use of MODEM:
Modem stands for MOdulator/DEModulator. A modem converts digital signals generated by the computer into analog signals which can be transmitted over a telephone or cable line and transforms incoming analog signals into their digital equivalents.
History of Modems
The first devices called modems converted digital data for transmission over analog telephone lines. The speed of these modems was measured in baud (a unit of measurement named after Emile Baudot), although as computer technology developed, these measures were converted into bits per second. The first commercial modems supported a speed of 110 bps and were used by the U.S. Department of Defense, news services, and some large businesses.
Modems gradually became familiar to consumers in the late 1970s through the 1980s as public message boards and news services like CompuServe were built on early internet infrastructure. Then, with the explosion of the World Wide Web in the mid and late 1990s, dial-up modems emerged as the primary form of internet access in many households around the world.
A modem is a device that provides access to the Internet.
As you know modem is common network device which is used to build connection from computer to Internet, but there are different types of modem available on market, and you might wonder about the difference between them.
DSL Modem
DSL modem is a network device that can be used to connect your computer to Internet via DSL (Digital Subscriber Line) connection. Nowadays it’s common to find router with built-in DSL modem feature too, and so it could be connected to multiple computers to connect to Internet at the same time.
is a network device that can be used to connect your computer to Internet via DSL (Digital Subscriber Line) connection. Nowadays it’s common to find router with built-in DSL modem feature too, and so it could be connected to multiple computers to connect to Internet at the same time.
Cable modem
You need to have cable modem if you want to establish high speed cable Internet connection, and this service is usually provided by cable TV provider. Sometimes newer set-top box is built with cable modem feature, so in this case you don’t need a separate cable modem.
if you want to establish high speed cable Internet connection, and this service is usually provided by cable TV provider. Sometimes newer set-top box is built with cable modem feature, so in this case you don’t need a separate cable modem.
Dial Up Modem
Dial up modem is used for establishing dial up Internet connection from computer or laptop by using telephone line. It’s not popular anymore as it’s pretty slow with up to 56Kbps transmission speed only, but it’s still used in rural areas with no other better Internet connection service or as backup connection. In addition, most of dial up modems also allows you to connect it to the fax machine for faxing purpose.
is used for establishing dial up Internet connection from computer or laptop by using telephone line. It’s not popular anymore as it’s pretty slow with up to 56Kbps transmission speed only, but it’s still used in rural areas with no other better Internet connection service or as backup connection. In addition, most of dial up modems also allows you to connect it to the fax machine for faxing purpose.
Broadband Modems
A broadband modem like those used for DSL or cable internet access uses advanced signaling techniques to achieve dramatically higher network speeds than earlier-generation dial-up modems. Broadband modems are often referred to as high-speed modems. Cellular modems are a type of digital modem that establishes internet connectivity between a mobile device and a cell phone network.
**********************************************************************
8) TCP/IP Protocols:
Protocols are sets of rules for message formats and procedures that allow machines and application programs to exchange information. These rules must be followed by each machine involved in the communication in order for the receiving host to be able to understand the message. The TCP/IP suite of protocols can be understood in terms of layers (or levels).
This figure depicts the layers of the TCP/IP protocol. From the top they are, Application Layer, Transport Layer, Network Layer, Network Interface Layer, and Hardware.

TCP/IP carefully defines how information moves from sender to receiver. First, application programs send messages or streams of data to one of the Internet Transport Layer Protocols, either the User Datagram Protocol (UDP) or the Transmission Control Protocol (TCP). These protocols receive the data from the application, divide it into smaller pieces called packets, add a destination address, and then pass the packets along to the next protocol layer, the Internet Network layer.
The Internet Network layer encloses the packet in an Internet Protocol (IP) datagram, puts in the datagram header and trailer, decides where to send the datagram (either directly to a destination or else to a gateway), and passes the datagram on to the Network Interface layer.
The Network Interface layer accepts IP datagrams and transmits them as frames over a specific network hardware, such as Ethernet or Token-Ring networks.
**************
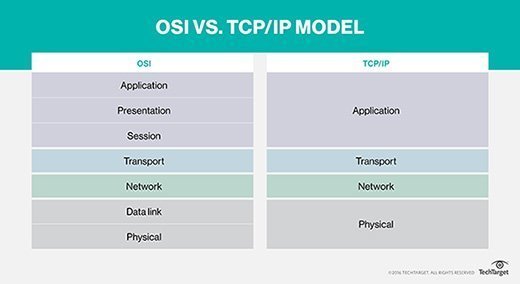
The TCP/IP model is a concise version of the OSI model. It contains four layers, unlike seven layers in the OSI model. The layers are:
- Process/Application Layer
- Host-to-Host/Transport Layer
- Internet Layer
- Network Access/Link Layer
The diagrammatic comparison of the TCP/IP and OSI model is as follows :
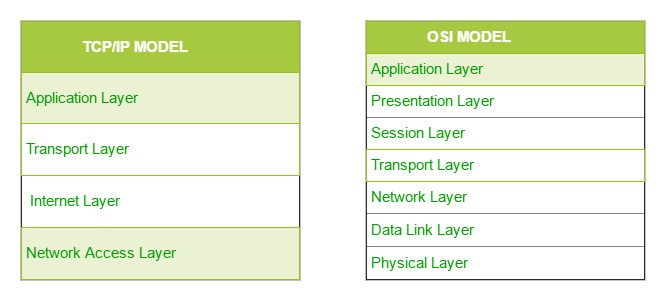
Difference between TCP/IP and OSI Model:
| TCP/IP | OSI |
|---|---|
| TCP refers to Transmission Control Protocol. | OSI refers to Open Systems Interconnection. |
| TCP/IP has 4 layers. | OSI has 7 layers. |
| TCP/IP is more reliable | OSI is less reliable |
| TCP/IP does not have very strict boundaries. | OSI has strict boundaries |
| TCP/IP follow a horizontal approach. | OSI follows a vertical approach. |
| TCP/IP uses both session and presentation layer in the application layer itself. | OSI uses different session and presentation layers. |
| TCP/IP developed protocols then model. | OSI developed model then protocol. |
The first layer is the Process layer on the behalf of the sender and Network Access layer on the behalf of the receiver. During this article, we will be talking on the behalf of the receiver.
1. Network Access Layer –
This layer corresponds to the combination of Data Link Layer and Physical Layer of the OSI model. It looks out for hardware addressing and the protocols present in this layer allows for the physical transmission of data.
We just talked about ARP being a protocol of Internet layer, but there is a conflict about declaring it as a protocol of Internet Layer or Network access layer. It is described as residing in layer 3, being encapsulated by layer 2 protocols.
We just talked about ARP being a protocol of Internet layer, but there is a conflict about declaring it as a protocol of Internet Layer or Network access layer. It is described as residing in layer 3, being encapsulated by layer 2 protocols.
2. Internet Layer –
This layer parallels the functions of OSI’s Network layer. It defines the protocols which are responsible for logical transmission of data over the entire network. The main protocols residing at this layer are :
- IP – stands for Internet Protocol and it is responsible for delivering packets from the source host to the destination host by looking at the IP addresses in the packet headers. IP has 2 versions:
IPv4 and IPv6. IPv4 is the one that most of the websites are using currently. But IPv6 is growing as the number of IPv4 addresses are limited in number when compared to the number of users. - ICMP – stands for Internet Control Message Protocol. It is encapsulated within IP datagrams and is responsible for providing hosts with information about network problems.
- ARP – stands for Address Resolution Protocol. Its job is to find the hardware address of a host from a known IP address. ARP has several types: Reverse ARP, Proxy ARP, Gratuitous ARP and Inverse ARP.
3. Host-to-Host Layer –
This layer is analogous to the transport layer of the OSI model. It is responsible for end-to-end communication and error-free delivery of data. It shields the upper-layer applications from the complexities of data. The two main protocols present in this layer are :
- Transmission Control Protocol (TCP) – It is known to provide reliable and error-free communication between end systems. It performs sequencing and segmentation of data. It also has acknowledgment feature and controls the flow of the data through flow control mechanism. It is a very effective protocol but has a lot of overhead due to such features. Increased overhead leads to increased cost.
- User Datagram Protocol (UDP) – On the other hand does not provide any such features. It is the go-to protocol if your application does not require reliable transport as it is very cost-effective. Unlike TCP, which is connection-oriented protocol, UDP is connectionless.
- HTTP and HTTPS – HTTP stands for Hypertext transfer protocol. It is used by the World Wide Web to manage communications between web browsers and servers. HTTPS stands for HTTP-Secure. It is a combination of HTTP with SSL(Secure Socket Layer). It is efficient in cases where the browser need to fill out forms, sign in, authenticate and carry out bank transactions.
- SSH – SSH stands for Secure Shell. It is a terminal emulations software similar to Telnet. The reason SSH is more preferred is because of its ability to maintain the encrypted connection. It sets up a secure session over a TCP/IP connection.
- NTP – NTP stands for Network Time Protocol. It is used to synchronize the clocks on our computer to one standard time source. It is very useful in situations like bank transactions. Assume the following situation without the presence of NTP. Suppose you carry out a transaction, where your computer reads the time at 2:30 PM while the server records it at 2:28 PM. The server can crash very badly if it’s out of sync.
4. Process Layer –
This layer performs the functions of top three layers of the OSI model: Application, Presentation and Session Layer. It is responsible for node-to-node communication and controls user-interface specifications. Some of the protocols present in this layer are: HTTP, HTTPS, FTP, TFTP, Telnet, SSH, SMTP, SNMP, NTP, DNS, DHCP, NFS, X Window, LPD. Have a look at Protocols in Application Layer for some information about these protocols. Protocols other than those present in the linked article are :
*********************************************************************
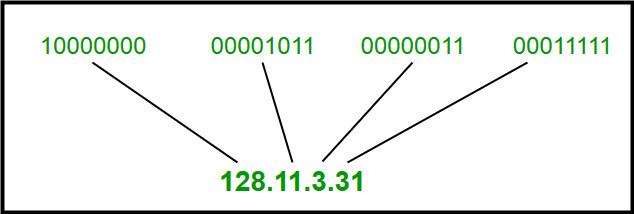
9) IP Addressing:
An Internet Protocol address (IP address) is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication.[1][2] An IP address serves two main functions: host or network interface identification and location addressing.
Each device connected to the internet has a unique identifier. Most networks today, including all computers on the internet, use the TCP/IP as a standard to communicate on the network. In the TCP/IP protocol, this unique identifier is the IP Address. The two kinds of IP Addresses are IPv4and IPv6.
IPv4 vs IPv6
IPv4 uses 32 binary bits to create a single unique address on the network. An IPv4 address is expressed by four numbers separated by dots. Each number is the decimal (base-10) representation for an eight-digit binary (base-2) number, also called an octet.


IPv6 uses 128 binary bits to create a single unique address on the network. An IPv6 address is expressed by eight groups of hexadecimal (base-16) numbers separated by colons. Groups of numbers that contain all zeros are often omitted to save space, leaving a colon separator to mark the gap .


IPv6 space is much larger than the IPv4 space due the use of hexadecimals as well as having 8 groups. Most devices use IPv4. However, due to advent of IoT devices and the greater demand for IP Addresses, more and more devices are accepting IPv6.
Static vs Dynamic
How does your computer get its IP address? An IP address can be either dynamic or static.


Static address is one that you configure yourself by editing your computer’s network settings. This type of address is rare, and it can create network issues if you use it without a good understanding of TCP/IP.
Dynamic addresses are the most common. They’re assigned by the Dynamic Host Configuration Protocol (DHCP), a service running on the network. DHCP typically runs on network hardware such as routers or dedicated DHCP servers. Dynamic IP addresses are issued using a leasing system, meaning that the IP address is only active for a limited time. If the lease expires, the computer will automatically request a new lease.
IP Classes
Typically, the IPv4 space allows us to have addresses between 0.0.0.0 to 255.255.255.255. However, some numbers in that range are reserved for specific purposes on TCP/IP networks. These reservations are recognized by the authority on TCP/IP addressing, the Internet Assigned Numbers Authority (IANA). Four specific reservations include the following:
- 0.0.0.0 — This represents the default network, which is the abstract concept of just being connected to a TCP/IP network.
- 255.255.255.255 — This address is reserved for network broadcasts, or messages that should go to all computers on the network.
- 127.0.0.1 — This is called the loopback address, meaning your computer’s way of identifying itself, whether or not it has an assigned IP address.
- 169.254.0.1 to 169.254.255.254 — This is the Automatic Private IP Addressing (APIPA) range of addresses assigned automatically when a computer’s unsuccessful getting an address from a DHCP server.
The other IP address reservations are for subnet classes. A subnet is a smaller network of computers connected to a larger network through a router. The subnet can have its own address system so computers on the same subnet can communicate quickly without sending data across the larger network. A router on a TCP/IP network, including the Internet, is configured to recognize one or more subnets and route network traffic appropriately. The following are the IP addresses reserved for subnets:
- 10.0.0.0 to 10.255.255.255 — This falls within the Class A address range of 1.0.0.0 to 127.0.0.0, in which the first bit is 0.
- 172.16.0.0 to 172.31.255.255 — This falls within the Class B address range of 128.0.0.0 to 191.255.0.0, in which the first two bits are 10.
- 192.168.0.0 to 192.168.255.255 — This falls within the Class C range of 192.0.0.0 through 223.255.255.0, in which the first three bits are 110.
- Multicast (formerly called Class D) — The first four bits in the address are 1110, with addresses ranging from 224.0.0.0 to 239.255.255.255.
- Reserved for future/experimental use (formerly called Class E) — addresses 240.0.0.0 to 254.255.255.254.
The first three (within Classes A, B and C) are those most used in creating subnets. Later, we’ll see how a subnet uses these addresses. The IANA has outlined specific uses for multicast addresses within Internet Engineering Task Force (IETF) document RFC 5771. However, it hasn’t designated a purpose or future plan for Class E addresses since it reserved the block in its 1989 document RFC 1112. Before IPv6, the Internet was filled with debate about whether the IANA should release Class E for general use.
*****
IP address is an address having information about how to reach a specific host, especially outside the LAN. An IP address is a 32 bit unique address having an address space of 232.
Generally, there are two notations in which IP address is written, dotted decimal notation and hexadecimal notation.
Generally, there are two notations in which IP address is written, dotted decimal notation and hexadecimal notation.
Some points to be noted about dotted decimal notation :
1. The value of any segment (byte) is between 0 and 255 (both included).
2. There are no zeroes preceding the value in any segment (054 is wrong, 54 is correct).
1. The value of any segment (byte) is between 0 and 255 (both included).
2. There are no zeroes preceding the value in any segment (054 is wrong, 54 is correct).
Classful Addressing
The 32 bit IP address is divided into five sub-classes. These are:
The 32 bit IP address is divided into five sub-classes. These are:
- Class A
- Class B
- Class C
- Class D
- Class E
Each of these classes has a valid range of IP addresses. Classes D and E are reserved for multicast and experimental purposes respectively. The order of bits in the first octet determine the classes of IP address.
IPv4 address is divided into two parts:
IPv4 address is divided into two parts:
- Network ID
- Host ID
The class of IP address is used to determine the bits used for network ID and host ID and the number of total networks and hosts possible in that particular class. Each ISP or network administrator assigns IP address to each device that is connected to its network.
Note: IP addresses are globally managed by Internet Assigned Numbers Authority(IANA) and regional Internet registries(RIR).
Note: While finding the total number of host IP addresses, 2 IP addresses are not counted and are therefore, decreased from the total count because the first IP address of any network is the network number and whereas the last IP address is reserved for broadcast IP.
Class A:
IP address belonging to class A are assigned to the networks that contain a large number of hosts.
- The network ID is 8 bits long.
- The host ID is 24 bits long.
The higher order bit of the first octet in class A is always set to 0. The remaining 7 bits in first octet are used to determine network ID. The 24 bits of host ID are used to determine the host in any network. The default subnet mask for class A is 255.x.x.x. Therefore, class A has a total of:
- 2^7-2= 126 network ID(Here 2 address is subracted because 0.0.0.0 and 127.x.y.z are special address. )
- 2^24 – 2 = 16,777,214 host ID
Class B:
IP address belonging to class B are assigned to the networks that ranges from medium-sized to large-sized networks.
- The network ID is 16 bits long.
- The host ID is 16 bits long.
The higher order bits of the first octet of IP addresses of class B are always set to 10. The remaining 14 bits are used to determine network ID. The 16 bits of host ID is used to determine the host in any network. The default sub-net mask for class B is 255.255.x.x. Class B has a total of:
- 2^14 = 16384 network address
- 2^16 – 2 = 65534 host address
- The network ID is 24 bits long.
- The host ID is 8 bits long.
- 2^21 = 2097152 network address
- 2^8 – 2 = 254 host address
- Within any network, the host ID must be unique to that network.
- Host ID in which all bits are set to 0 cannot be assigned because this host ID is used to represent the network ID of the IP address.
- Host ID in which all bits are set to 1 cannot be assigned because this host ID is reserved as a broadcast address to send packets to all the hosts present on that particular network.
- The network ID cannot start with 127 because 127 belongs to class A address and is reserved for internal loop-back functions.
- All bits of network ID set to 1 are reserved for use as an IP broadcast address and therefore, cannot be used.
- All bits of network ID set to 0 are used to denote a specific host on the local network and are not routed and therefore, aren’t used.
- Private IP Address: These are used "inside" a network, like the one you probably run at home, used by things like tablets, Wi-Fi cameras, wireless printers, desktops, etc. These types of IP addresses are used to provide a way for your devices to communicate with your router and all the other devices on your private network. Private IP addresses can be set manually or assigned automatically by your router.
- Public IP Address: These are used on the outside of your network and are assigned by your ISP. It's the main address that your home or business network uses to communicate with the rest of the networked devices around the world (i.e., the internet). It provides a way for the devices in your home, for example, to reach your ISP, and therefore the outside world, allowing them to do things like access websites and communicate directly with other computers and servers around the world.
- Linux: Linux users can launch a terminal window and enter the command hostname -I (that's a capital "i"), ifconfig, or ip addr show.
- MacOS: For macOS, use the command ifconfig to find your local IP address.
- iOS: iPhone, iPad, and iPod touch devices show their private IP address through the Settings app in the Wi-Fi menu. To see it, just tap the small "i" button next to the network it's connected to.
- Android: You can see the local IP address of an Android device through Settings > Network & internet > Wi-Fi, or depending on your Android version, Settings > Wi-Fi or Settings > Wireless Controls > Wi-Fi settings. Just tap the network you're on to see a new window that shows network information that includes the private IP address. You might have to expand an Advanced area of the network's details page to see the private IP address.
- IPv4: The way IPv4 addresses are constructed means it's able to provide over 4 billion unique IP addresses (232). While this is a very large number of addresses, it's not enough for the modern world with all the different devices people are using on the internet.
- IPv6: IPv6 supports a whopping 340 trillion, trillion, trillion addresses (2128). That's 340 with 12 zeros! This means every person on earth could connect billions of devices to the internet. True, this is a bit of an overkill, but you can see how effectively IPv6 solves this problem.
- No more IP address collisions caused by private addresses.
- Auto-configuration
- No reason for Network Address Translation (NAT)
- More efficient routing
- Easier administration
- Built-in privacy, and more.
- IP addresses belonging to class B ranges from 128.0.x.x – 191.255.x.x.
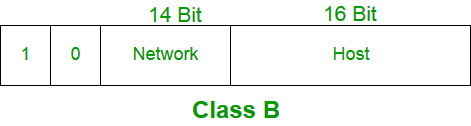
Class C:
IP address belonging to class C are assigned to small-sized networks.
The higher order bits of the first octet of IP addresses of class C are always set to 110. The remaining 21 bits are used to determine network ID. The 8 bits of host ID is used to determine the host in any network. The default sub-net mask for class C is 255.255.255.x. Class C has a total of:
Class D:
IP address belonging to class D are reserved for multi-casting. The higher order bits of the first octet of IP addresses belonging to class D are always set to 1110. The remaining bits are for the address that interested hosts recognize.
Class D does not posses any sub-net mask. IP addresses belonging to class D ranges from 224.0.0.0 – 239.255.255.255.


Class E:
IP addresses belonging to class E are reserved for experimental and research purposes. IP addresses of class E ranges from 240.0.0.0 – 255.255.255.254. This class doesn’t have any sub-net mask. The higher order bits of first octet of class E are always set to 1111.
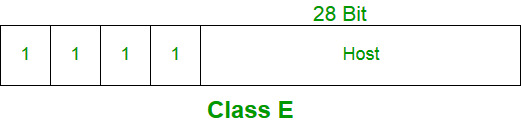

Range of special IP addresses:
169.254.0.0 – 169.254.0.16 : Link local addresses
127.0.0.0 – 127.0.0.8 : Loop-back addresses
0.0.0.0 – 0.0.0.8 : used to communicate within the current network.
127.0.0.0 – 127.0.0.8 : Loop-back addresses
0.0.0.0 – 0.0.0.8 : used to communicate within the current network.
Rules for assigning Host ID:
Host ID’s are used to identify a host within a network. The host ID are assigned based on the following rules:
Rules for assigning Network ID:
Hosts that are located on the same physical network are identified by the network ID, as all host on the same physical network is assigned the same network ID. The network ID is assigned based on the following rules:
Summary of Classful addressing :
Problems with Classful Addressing:
The problem with this classful addressing method is that millions of class A address are wasted, many of the class B address are wasted, whereas, number of addresses available in class C is so small that it cannot cater the needs of organizations. Class D addresses are used for multicast routing and are therefore available as a single block only. Class E addresses are reserved.
Since there are these problems, Classful networking was replaced by Classless Inter-Domain Routing (CIDR) in 1993.
What Is an IP Address Used For?
An IP address provides an identity to a networked device on the internet. Similar to a home or business address supplying a specific physical location with an identifiable address, devices on a network are differentiated from one another through IP addresses.
If you're going to send a package to your friend in another country, you have to know the exact destination. This same general process is used when sending data over the internet. However, instead of using a physical mailing address, your computer uses DNS servers to look up a hostname to find its IP address.
For example, when you enter a website URL like www.lifewire.com into your browser, your request to load that page is sent to DNS servers that look up the hostname of "lifewire.com" to find its corresponding IP address. Without the IP address, your computer would have no clue what it is that I'm after.
Different Types of IP Addresses
Even if you've heard of IP addresses before, you might not realize that there are specific types of IP addresses. While all IP addresses are made up of numbers or letters, not all addresses are used for the same purpose.
There are private IP addresses, public IP addresses, static IP addresses, and dynamic IP addresses. That's quite a variety!
To add to the complexity, each type of IP address can be an IPv4 address or an IPv6 address — again, more on these at the bottom of this page.
Both private IP addresses and public IP addresses are either dynamic or static, which means that, respectively, they either change or they don't.
An IP address that is assigned by a DHCP server is a dynamic IP address. If a device doesn't have DHCP enabled or doesn't support DHCP, then the IP address must be assigned manually, in which case it's called a static IP address.
What Is My IP Address?
Different devices and operating systems require unique steps to find the IP address. There are also different steps to take if you're looking for the public IP address provided to you by your ISP, or if you need to see the private IP address that your router assigned to your device.
PUBLIC IP ADDRESS
There are lots of ways to find your router's public IP address, but sites like IP Chicken, WhatsMyIP.org, WhatIsMyIPAddress.com, or icanhazip.com make this super easy. These sites work on any network-connected device that supports a web browser, like your smartphone, iPod, laptop, desktop, tablet, etc.
Another good way to find your external IP address in Windows is using the following command in the Command Prompt:
PRIVATE IP ADDRESS
:max_bytes(150000):strip_icc():format(webp)/001_2625920-5b871e10c9e77c00257f6dc4.jpg)
In Windows, you can find your device's local IP address via the Command Prompt, using the ipconfig command.
See how do I find my default gateway IP address? if you need to find the IP address of your router, or whatever device that your network uses to access the public internet.
IP Versions (IPv4 vs IPv6)
There are two versions of IP: internet protocol version 4 (IPv4) and Internet protocol version 6 (IPv6). If you've heard of these terms, you probably know that the former is the older version, while IPv6 is the upgraded IP version.
One reason IPv6 is replacing IPv4 is that it can provide a much larger number of IP addresses than IPv4 allows. With all the devices you may have constantly connected to the internet, it's important that there's a unique address available for each one of them.
Visualizing this helps understand just how many more IP addresses the IPv6 addressing scheme allows over IPv4. Pretend a postage stamp could provide enough space to hold each and every IPv4 address. IPv6, then, to scale, would need the entire solar system to contain all of its addresses.
:max_bytes(150000):strip_icc():format(webp)/hat-is-an-ip-address-2625920-4-eb8b369180c74223874921d68a086dd8.png)
In addition to the greater supply of IP addresses over IPv4, IPv6 has the following added benefits:
IPv4 displays addresses as a 32-bit numerical number written in decimal format, like 207.241.148.80 or 192.168.1.1.
Because there are trillions of possible IPv6 addresses, they must be written in hexadecimal to display them, like 3ffe:1900:4545:3:200:f8ff:fe21:67cf.
Was this page helpful?
NEXT UP:
IP Addresses 101
**********************************************************************
10) Domain Name System:
When DNS was not into existence, one had to download a Host filecontaining host names and their corresponding IP address. But with increase in number of hosts of internet, the size of host file also increased. This resulted in increased traffic on downloading this file. To solve this problem the DNS system was introduced.
Domain Name System helps to resolve the host name to an address. It uses a hierarchical naming scheme and distributed database of IP addresses and associated names
IP Address
IP address is a unique logical address assigned to a machine over the network. An IP address exhibits the following properties:
- IP address is the unique address assigned to each host present on Internet.
- IP address is 32 bits (4 bytes) long.
- IP address consists of two components: network component and host component.
- Each of the 4 bytes is represented by a number from 0 to 255, separated with dots. For example 137.170.4.124
IP address is 32-bit number while on the other hand domain names are easy to remember names. For example, when we enter an email address we always enter a symbolic string such as webmaster@tutorialspoint.com.
Uniform Resource Locator (URL)
Uniform Resource Locator (URL) refers to a web address which uniquely identifies a document over the internet.
This document can be a web page, image, audio, video or anything else present on the web.
For example, www.tutorialspoint.com/internet_technology/index.htmlis an URL to the index.html which is stored on tutorialspoint web server under internet_technology directory.
URL Types
There are two forms of URL as listed below:
- Absolute URL
- Relative URL
ABSOLUTE URL
Absolute URL is a complete address of a resource on the web. This completed address comprises of protocol used, server name, path name and file name.
For example http:// www.tutorialspoint.com / internet_technology /index.htm. where:
- http is the protocol.
- tutorialspoint.com is the server name.
- index.htm is the file name.
The protocol part tells the web browser how to handle the file. Similarly we have some other protocols also that can be used to create URL are:
- FTP
- https
- Gopher
- mailto
- news
RELATIVE URL
Relative URL is a partial address of a webpage. Unlike absolute URL, the protocol and server part are omitted from relative URL.
Relative URLs are used for internal links i.e. to create links to file that are part of same website as the WebPages on which you are placing the link.
For example, to link an image on tutorialspoint.com/internet_technology/internet_referemce_models, we can use the relative URL which can take the form like /internet_technologies/internet-osi_model.jpg.
Difference between Absolute and Relative URL
| Absolute URL | Relative URL |
|---|---|
| Used to link web pages on different websites | Used to link web pages within the same website. |
| Difficult to manage. | Easy to Manage |
| Changes when the server name or directory name changes | Remains same even of we change the server name or directory name. |
| Take time to access | Comparatively faster to access. |
Domain Name System Architecture
The Domain name system comprises of Domain Names, Domain Name Space, Name Server that have been described below:
Domain Names
Domain Name is a symbolic string associated with an IP address. There are several domain names available; some of them are generic such as com, edu, gov, net etc, while some country level domain names such as au, in, za, usetc.
The following table shows the Generic Top-Level Domain names:
| Domain Name | Meaning |
|---|---|
| Com | Commercial business |
| Edu | Education |
| Gov | U.S. government agency |
| Int | International entity |
| Mil | U.S. military |
| Net | Networking organization |
| Org | Non profit organization |
The following table shows the Country top-level domain names:
| Domain Name | Meaning |
|---|---|
| au | Australia |
| in | India |
| cl | Chile |
| fr | France |
| us | United States |
| za | South Africa |
| uk | United Kingdom |
| jp | Japan |
| es | Spain |
| de | Germany |
| ca | Canada |
| ee | Estonia |
| hk | Hong Kong |
Domain Name Space
The domain name space refers a hierarchy in the internet naming structure. This hierarchy has multiple levels (from 0 to 127), with a root at the top. The following diagram shows the domain name space hierarchy:
In the above diagram each subtree represents a domain. Each domain can be partitioned into sub domains and these can be further partitioned and so on.
Name Server
Name server contains the DNS database. This database comprises of various names and their corresponding IP addresses. Since it is not possible for a single server to maintain entire DNS database, therefore, the information is distributed among many DNS servers.
Zones
Zone is collection of nodes (sub domains) under the main domain. The server maintains a database called zone file for every zone.
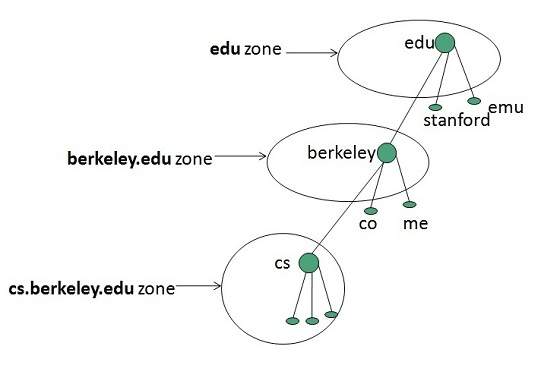
If the domain is not further divided into sub domains then domain and zone refers to the same thing.
The information about the nodes in the sub domain is stored in the servers at the lower levels however; the original server keeps reference to these lower levels of servers.
TYPES OF NAME SERVERS
Following are the three categories of Name Servers that manages the entire Domain Name System:
- Root Server
- Primary Server
- Secondary Server
ROOT SERVER
Root Server is the top level server which consists of the entire DNS tree. It does not contain the information about domains but delegates the authority to the other server
PRIMARY SERVERS
Primary Server stores a file about its zone. It has authority to create, maintain, and update the zone file.
SECONDARY SERVER
Secondary Server transfers complete information about a zone from another server which may be primary or secondary server. The secondary server does not have authority to create or update a zone file.
DNS Working
DNS translates the domain name into IP address automatically. Following steps will take you through the steps included in domain resolution process:
- When we type www.tutorialspoint.com into the browser, it asks the local DNS Server for its IP address.
- When the local DNS does not find the IP address of requested domain name, it forwards the request to the root DNS server and again enquires about IP address of it.
- The root DNS server replies with delegation that I do not know the IP address of www.tutorialspoint.com but know the IP address of DNS Server.
- The local DNS server then asks the com DNS Server the same question.
- The com DNS Server replies the same that it does not know the IP address of www.tutorialspont.com but knows the address of tutorialspoint.com.
- Then the local DNS asks the tutorialspoint.com DNS server the same question.
- Then tutorialspoint.com DNS server replies with IP address of www.tutorialspoint.com.
- Now, the local DNS sends the IP address of www.tutorialspoint.com to the computer that sends the request.
Here the local DNS is at ISP end.
**********************************************************************
11) URL:
Definition: URL is an acronym for Uniform Resource Locator and is a reference (an address) to a resource on the Internet.
A URL has two main components:
- Protocol identifier: For the URL
http://example.com, the protocol identifier ishttp. - Resource name: For the URL
http://example.com, the resource name isexample.com.
Note that the protocol identifier and the resource name are separated by a colon and two forward slashes. The protocol identifier indicates the name of the protocol to be used to fetch the resource. The example uses the Hypertext Transfer Protocol (HTTP), which is typically used to serve up hypertext documents. HTTP is just one of many different protocols used to access different types of resources on the net. Other protocols include File Transfer Protocol (FTP), Gopher, File, and News.
The resource name is the complete address to the resource. The format of the resource name depends entirely on the protocol used, but for many protocols, including HTTP, the resource name contains one or more of the following components:
- Host Name
- The name of the machine on which the resource lives.
- Filename
- The pathname to the file on the machine.
- Port Number
- The port number to which to connect (typically optional).
- Reference
- A reference to a named anchor within a resource that usually identifies a specific location within a file (typically optional).
For many protocols, the host name and the filename are required, while the port number and reference are optional. For example, the resource name for an HTTP URL must specify a server on the network (Host Name) and the path to the document on that machine (Filename); it also can specify a port number and a reference.
URL is the abbreviation of Uniform Resource Locator and is defined as the global address of documents and other resources on the World Wide Web. To visit this website, for example, you'll go to the URL www.webopedia.com.
We all use URLs to visit webpages and other resources on the web. The URL is an address that sends users to a specific resource online, such as a webpage, video or other document or resource. When you search Google, for example, the search results will display the URL of the resources that match your search query. The title in search results is simply a hyperlink to the URL of the resource.
A URL is one type of Uniform Resource Identifier (URI); the generic term for all types of names and addresses that refer to objects on the World Wide Web.
What Are the Parts of a URL?
The first part of the URL is called a protocol identifier and it indicates what protocol to use, and the second part is called a resource name and it specifies the IP address or the domain name where the resource is located. The protocol identifier and the resource name are separated by a colon and two forward slashes.
For example, the two URLs below point to two different files at the domain webopedia.com. The first specifies an executable file that should be fetched using the FTP protocol; the second specifies a webpage that should be fetched using the HTTP protocol:
ftp://www.webopedia.com/stuff.exe
http://www.webopedia.com/index.html
Web Address is a URL with HTTP/HTTPS
The term "web address" is a synonym for a URL that uses the HTTP or HTTPS protocol. The Uniform Resource Locator (URL) was developed by Tim Berners-Lee in 1994 and the Internet Engineering Task Force (IETF) URI working group. Today, the format of the URL has not changed. The URL format is specified in RFC 1738 Uniform Resource Locators (URL).
In Programming: The URL Class
Note that in object-oriented programming, such as Java, programs can use a class (a category of objects) called URL. You can create a URL object to represent the URL address. See Java Tutorials: Working with URLs in the Related Links section below for additional information on using the URL object in a Java program.
***********************************************************************
12) Introduction to Internet:
************************************************************************
13) HTML:-
**********************************************************************
**********************************************************************